

SUBSCRIBE TO OUR FREE NEWSLETTER
Daily news & progressive opinion—funded by the people, not the corporations—delivered straight to your inbox.
5
#000000
#FFFFFF
To donate by check, phone, or other method, see our More Ways to Give page.


Daily news & progressive opinion—funded by the people, not the corporations—delivered straight to your inbox.
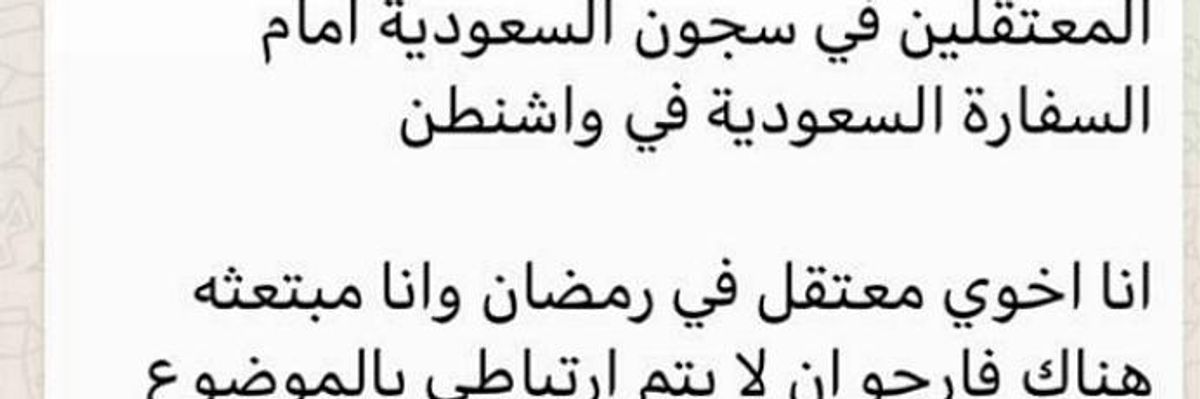
An Amnesty International staffer received an anonymous message in Arabic that said in part, "Can you please cover [the protest] for your brothers detained in Saudi Arabia in front of the Saudi embassy in Washington. My brother is detained in Ramadan and I am on a scholarship here so please do not link me to this." (Photo: Amnesty International)
An investigation published Wednesday by the London-based Amnesty International revealed that one of the group's staffers was "targeted by a sophisticated surveillance campaign, in what the organization suspects was a deliberate attempt to spy on its staff by a government hostile to its work," using a tool developed by the Israeli cyber intelligence firm NSO Group.
"The message sent to us seems to be part of a much broader surveillance campaign, which we suspect is being used to spy on human rights activists worldwide and prevent their vital work."
--Joshua Franco, Amnesty International
In early June--while Amnesty was campaigning for the release of six women's rights activists jailed in Saudi Arabia--a staff member received an anonymous message in Arabic on the smartphone application WhatsApp from someone who claimed their brother was detained in Saudi Arabia and requested that the group "cover" a protest in front of the Saudi embassy in Washington, D.C.
Through its investigation, Amnesty discovered that if the staffer had clicked a link included in the message, they would have unknowingly installed NSO Group's "extraordinarily invasive" Pegasus program on their smartphone.
As Joshua Franco, Amnesty International's head of technology and human rights, explained, "a smartphone infected with Pegasus is essentially controlled by the attacker--it can relay phone calls, photos, messages, and more directly to the operator."
"NSO Group is known to only sell its spyware to governments. We therefore believe that this was a deliberate attempt to infiltrate Amnesty International by a government hostile to our human rights work," Franco said. "This chilling attack on Amnesty International highlights the grave risk posed to activists around the world by this kind of surveillance technology."
\u201cA malicious WhatsApp message with #SaudiArabia-related bait content, carrying links we believe are used to infect victims with highly sophisticated mobile spyware, were sent to our staff member. Read our full investigation here. \n\nhttps://t.co/TkzSMp8BXG\u201d— Amnesty International (@Amnesty International) 1533114934
Amnesty also found that another Saudi Arabia rights activist had received a similar message, and subsequent investigations "revealed that the domain link in the message belongs to a large infrastructure of more than 600 suspicious websites which had been previously connected to NSO Group." The group expressed concern that this apparent scheme "could be used to bait and spy on activists in countries including Kenya, Democratic Republic of Congo, and Hungary, in addition to the Gulf."
"The message sent to us seems to be part of a much broader surveillance campaign, which we suspect is being used to spy on human rights activists worldwide and prevent their vital work," Franco warned. "We are working with human rights activists to help them protect themselves against similar cowardly attacks, and ensure that abusive governments cannot use technology to silence them."
In a statement to Amnesty, NSO Group said the company "develops cyber technology to allow government agencies to identify and disrupt terrorist and criminal plots. Our product is intended to be used exclusively for the investigation and prevention of crime and terrorism. Any use of our technology that is counter to that purpose is a violation of our policies, legal contracts, and the values that we stand for as a company."
Trump and Musk are on an unconstitutional rampage, aiming for virtually every corner of the federal government. These two right-wing billionaires are targeting nurses, scientists, teachers, daycare providers, judges, veterans, air traffic controllers, and nuclear safety inspectors. No one is safe. The food stamps program, Social Security, Medicare, and Medicaid are next. It’s an unprecedented disaster and a five-alarm fire, but there will be a reckoning. The people did not vote for this. The American people do not want this dystopian hellscape that hides behind claims of “efficiency.” Still, in reality, it is all a giveaway to corporate interests and the libertarian dreams of far-right oligarchs like Musk. Common Dreams is playing a vital role by reporting day and night on this orgy of corruption and greed, as well as what everyday people can do to organize and fight back. As a people-powered nonprofit news outlet, we cover issues the corporate media never will, but we can only continue with our readers’ support. |
An investigation published Wednesday by the London-based Amnesty International revealed that one of the group's staffers was "targeted by a sophisticated surveillance campaign, in what the organization suspects was a deliberate attempt to spy on its staff by a government hostile to its work," using a tool developed by the Israeli cyber intelligence firm NSO Group.
"The message sent to us seems to be part of a much broader surveillance campaign, which we suspect is being used to spy on human rights activists worldwide and prevent their vital work."
--Joshua Franco, Amnesty International
In early June--while Amnesty was campaigning for the release of six women's rights activists jailed in Saudi Arabia--a staff member received an anonymous message in Arabic on the smartphone application WhatsApp from someone who claimed their brother was detained in Saudi Arabia and requested that the group "cover" a protest in front of the Saudi embassy in Washington, D.C.
Through its investigation, Amnesty discovered that if the staffer had clicked a link included in the message, they would have unknowingly installed NSO Group's "extraordinarily invasive" Pegasus program on their smartphone.
As Joshua Franco, Amnesty International's head of technology and human rights, explained, "a smartphone infected with Pegasus is essentially controlled by the attacker--it can relay phone calls, photos, messages, and more directly to the operator."
"NSO Group is known to only sell its spyware to governments. We therefore believe that this was a deliberate attempt to infiltrate Amnesty International by a government hostile to our human rights work," Franco said. "This chilling attack on Amnesty International highlights the grave risk posed to activists around the world by this kind of surveillance technology."
\u201cA malicious WhatsApp message with #SaudiArabia-related bait content, carrying links we believe are used to infect victims with highly sophisticated mobile spyware, were sent to our staff member. Read our full investigation here. \n\nhttps://t.co/TkzSMp8BXG\u201d— Amnesty International (@Amnesty International) 1533114934
Amnesty also found that another Saudi Arabia rights activist had received a similar message, and subsequent investigations "revealed that the domain link in the message belongs to a large infrastructure of more than 600 suspicious websites which had been previously connected to NSO Group." The group expressed concern that this apparent scheme "could be used to bait and spy on activists in countries including Kenya, Democratic Republic of Congo, and Hungary, in addition to the Gulf."
"The message sent to us seems to be part of a much broader surveillance campaign, which we suspect is being used to spy on human rights activists worldwide and prevent their vital work," Franco warned. "We are working with human rights activists to help them protect themselves against similar cowardly attacks, and ensure that abusive governments cannot use technology to silence them."
In a statement to Amnesty, NSO Group said the company "develops cyber technology to allow government agencies to identify and disrupt terrorist and criminal plots. Our product is intended to be used exclusively for the investigation and prevention of crime and terrorism. Any use of our technology that is counter to that purpose is a violation of our policies, legal contracts, and the values that we stand for as a company."
An investigation published Wednesday by the London-based Amnesty International revealed that one of the group's staffers was "targeted by a sophisticated surveillance campaign, in what the organization suspects was a deliberate attempt to spy on its staff by a government hostile to its work," using a tool developed by the Israeli cyber intelligence firm NSO Group.
"The message sent to us seems to be part of a much broader surveillance campaign, which we suspect is being used to spy on human rights activists worldwide and prevent their vital work."
--Joshua Franco, Amnesty International
In early June--while Amnesty was campaigning for the release of six women's rights activists jailed in Saudi Arabia--a staff member received an anonymous message in Arabic on the smartphone application WhatsApp from someone who claimed their brother was detained in Saudi Arabia and requested that the group "cover" a protest in front of the Saudi embassy in Washington, D.C.
Through its investigation, Amnesty discovered that if the staffer had clicked a link included in the message, they would have unknowingly installed NSO Group's "extraordinarily invasive" Pegasus program on their smartphone.
As Joshua Franco, Amnesty International's head of technology and human rights, explained, "a smartphone infected with Pegasus is essentially controlled by the attacker--it can relay phone calls, photos, messages, and more directly to the operator."
"NSO Group is known to only sell its spyware to governments. We therefore believe that this was a deliberate attempt to infiltrate Amnesty International by a government hostile to our human rights work," Franco said. "This chilling attack on Amnesty International highlights the grave risk posed to activists around the world by this kind of surveillance technology."
\u201cA malicious WhatsApp message with #SaudiArabia-related bait content, carrying links we believe are used to infect victims with highly sophisticated mobile spyware, were sent to our staff member. Read our full investigation here. \n\nhttps://t.co/TkzSMp8BXG\u201d— Amnesty International (@Amnesty International) 1533114934
Amnesty also found that another Saudi Arabia rights activist had received a similar message, and subsequent investigations "revealed that the domain link in the message belongs to a large infrastructure of more than 600 suspicious websites which had been previously connected to NSO Group." The group expressed concern that this apparent scheme "could be used to bait and spy on activists in countries including Kenya, Democratic Republic of Congo, and Hungary, in addition to the Gulf."
"The message sent to us seems to be part of a much broader surveillance campaign, which we suspect is being used to spy on human rights activists worldwide and prevent their vital work," Franco warned. "We are working with human rights activists to help them protect themselves against similar cowardly attacks, and ensure that abusive governments cannot use technology to silence them."
In a statement to Amnesty, NSO Group said the company "develops cyber technology to allow government agencies to identify and disrupt terrorist and criminal plots. Our product is intended to be used exclusively for the investigation and prevention of crime and terrorism. Any use of our technology that is counter to that purpose is a violation of our policies, legal contracts, and the values that we stand for as a company."