

SUBSCRIBE TO OUR FREE NEWSLETTER
Daily news & progressive opinion—funded by the people, not the corporations—delivered straight to your inbox.
5
#000000
#FFFFFF
To donate by check, phone, or other method, see our More Ways to Give page.


Daily news & progressive opinion—funded by the people, not the corporations—delivered straight to your inbox.
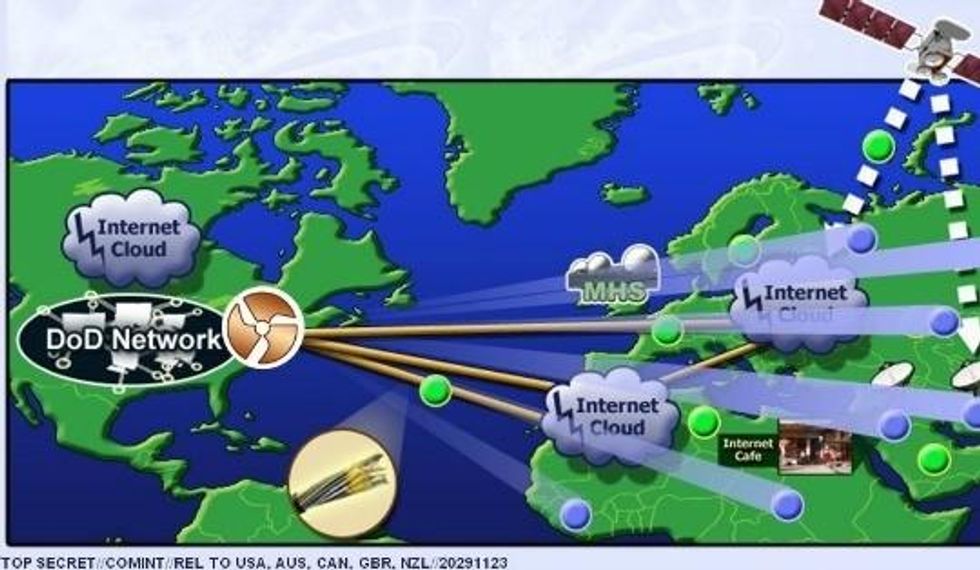
"This is huge, in scale and in implications."
"Disturbing."
Those are just some of the ways people are reacting to the latest reporting by journalists Glenn Greenwald and Ryan Gallagher at The Intercept on documents leaked by NSA whistleblower Edward Snowden.
In a news story entitled, 'How the NSA Plans to Infect 'Millions' of Computers with Malware," Greenwald and Gallager explore a series of internal NSA slides and documents showing just how dramatically the agency is "expanding its ability to covertly hack into computers on a mass scale." The revelations also show that the NSA has "aggressively accelerated its hacking initiatives" by supplanting operations once done manually by human operators with automated systems that "reduce the level of human oversight."
Among the most searing aspects of the involved and technical of the review of the NSA material, Greenwald and Gallagher explain how a series of sophisticated hacking programs use malware to perform both targeted infiltrations of computers but also broader mass surveillance over entire networks. The Intercept reports:
One implant, codenamed UNITEDRAKE, can be used with a variety of "plug-ins" that enable the agency to gain total control of an infected computer.
An implant plug-in named CAPTIVATEDAUDIENCE, for example, is used to take over a targeted computer's microphone and record conversations taking place near the device. Another, GUMFISH, can covertly take over a computer's webcam and snap photographs. FOGGYBOTTOM records logs of Internet browsing histories and collects login details and passwords used to access websites and email accounts. GROK is used to log keystrokes. And SALVAGERABBIT exfiltrates data from removable flash drives that connect to an infected computer.
The implants can enable the NSA to circumvent privacy-enhancing encryption tools that are used to browse the Internet anonymously or scramble the contents of emails as they are being sent across networks. That's because the NSA's malware gives the agency unfettered access to a target's computer before the user protects their communications with encryption.
It is unclear how many of the implants are being deployed on an annual basis or which variants of them are currently active in computer systems across the world.
Asked to comment by the journalists, Mikko Hypponen, an expert in malware who serves as chief research officer at the Finnish security firm F-Secure, said the implications of the NSA programs were "disturbing" as these kinds of clandestine manipulations can seriously impact the functioning of the web.
"When they deploy malware on systems," Hypponen explained, "they potentially create new vulnerabilities in these systems, making them more vulnerable for attacks by third parties."
The reporting also explains how the NSA has used what are called "man-in-the-middle" techniques as a way to trick computers into giving access to fake servers designed to look like friendly ones. In one example, under a program codenamed QUANTUMHAND, the NSA used a phony server that looked like it was a Facebook server so it could access users computers. According to the reporting:
When a target attempts to log in to the social media site, the NSA transmits malicious data packets that trick the target's computer into thinking they are being sent from the real Facebook. By concealing its malware within what looks like an ordinary Facebook page, the NSA is able to hack into the targeted computer and covertly siphon out data from its hard drive. A top-secret animation demonstrates the tactic in action.
The documents show that QUANTUMHAND became operational in October 2010, after being successfully tested by the NSA against about a dozen targets.
According to Matt Blaze, a surveillance and cryptography expert at the University of Pennsylvania, it appears that the QUANTUMHAND technique is aimed at targeting specific individuals. But he expresses concerns about how it has been covertly integrated within Internet networks as part of the NSA's automated TURBINE system.
"As soon as you put this capability in the backbone infrastructure, the software and security engineer in me says that's terrifying," Blaze says.
"Forget about how the NSA is intending to use it. How do we know it is working correctly and only targeting who the NSA wants? And even if it does work correctly, which is itself a really dubious assumption, how is it controlled?"
____________________________
Common Dreams is powered by optimists who believe in the power of informed and engaged citizens to ignite and enact change to make the world a better place. We're hundreds of thousands strong, but every single supporter makes the difference. Your contribution supports this bold media model—free, independent, and dedicated to reporting the facts every day. Stand with us in the fight for economic equality, social justice, human rights, and a more sustainable future. As a people-powered nonprofit news outlet, we cover the issues the corporate media never will. |

"This is huge, in scale and in implications."
"Disturbing."
Those are just some of the ways people are reacting to the latest reporting by journalists Glenn Greenwald and Ryan Gallagher at The Intercept on documents leaked by NSA whistleblower Edward Snowden.
In a news story entitled, 'How the NSA Plans to Infect 'Millions' of Computers with Malware," Greenwald and Gallager explore a series of internal NSA slides and documents showing just how dramatically the agency is "expanding its ability to covertly hack into computers on a mass scale." The revelations also show that the NSA has "aggressively accelerated its hacking initiatives" by supplanting operations once done manually by human operators with automated systems that "reduce the level of human oversight."
Among the most searing aspects of the involved and technical of the review of the NSA material, Greenwald and Gallagher explain how a series of sophisticated hacking programs use malware to perform both targeted infiltrations of computers but also broader mass surveillance over entire networks. The Intercept reports:
One implant, codenamed UNITEDRAKE, can be used with a variety of "plug-ins" that enable the agency to gain total control of an infected computer.
An implant plug-in named CAPTIVATEDAUDIENCE, for example, is used to take over a targeted computer's microphone and record conversations taking place near the device. Another, GUMFISH, can covertly take over a computer's webcam and snap photographs. FOGGYBOTTOM records logs of Internet browsing histories and collects login details and passwords used to access websites and email accounts. GROK is used to log keystrokes. And SALVAGERABBIT exfiltrates data from removable flash drives that connect to an infected computer.
The implants can enable the NSA to circumvent privacy-enhancing encryption tools that are used to browse the Internet anonymously or scramble the contents of emails as they are being sent across networks. That's because the NSA's malware gives the agency unfettered access to a target's computer before the user protects their communications with encryption.
It is unclear how many of the implants are being deployed on an annual basis or which variants of them are currently active in computer systems across the world.
Asked to comment by the journalists, Mikko Hypponen, an expert in malware who serves as chief research officer at the Finnish security firm F-Secure, said the implications of the NSA programs were "disturbing" as these kinds of clandestine manipulations can seriously impact the functioning of the web.
"When they deploy malware on systems," Hypponen explained, "they potentially create new vulnerabilities in these systems, making them more vulnerable for attacks by third parties."
The reporting also explains how the NSA has used what are called "man-in-the-middle" techniques as a way to trick computers into giving access to fake servers designed to look like friendly ones. In one example, under a program codenamed QUANTUMHAND, the NSA used a phony server that looked like it was a Facebook server so it could access users computers. According to the reporting:
When a target attempts to log in to the social media site, the NSA transmits malicious data packets that trick the target's computer into thinking they are being sent from the real Facebook. By concealing its malware within what looks like an ordinary Facebook page, the NSA is able to hack into the targeted computer and covertly siphon out data from its hard drive. A top-secret animation demonstrates the tactic in action.
The documents show that QUANTUMHAND became operational in October 2010, after being successfully tested by the NSA against about a dozen targets.
According to Matt Blaze, a surveillance and cryptography expert at the University of Pennsylvania, it appears that the QUANTUMHAND technique is aimed at targeting specific individuals. But he expresses concerns about how it has been covertly integrated within Internet networks as part of the NSA's automated TURBINE system.
"As soon as you put this capability in the backbone infrastructure, the software and security engineer in me says that's terrifying," Blaze says.
"Forget about how the NSA is intending to use it. How do we know it is working correctly and only targeting who the NSA wants? And even if it does work correctly, which is itself a really dubious assumption, how is it controlled?"
____________________________

"This is huge, in scale and in implications."
"Disturbing."
Those are just some of the ways people are reacting to the latest reporting by journalists Glenn Greenwald and Ryan Gallagher at The Intercept on documents leaked by NSA whistleblower Edward Snowden.
In a news story entitled, 'How the NSA Plans to Infect 'Millions' of Computers with Malware," Greenwald and Gallager explore a series of internal NSA slides and documents showing just how dramatically the agency is "expanding its ability to covertly hack into computers on a mass scale." The revelations also show that the NSA has "aggressively accelerated its hacking initiatives" by supplanting operations once done manually by human operators with automated systems that "reduce the level of human oversight."
Among the most searing aspects of the involved and technical of the review of the NSA material, Greenwald and Gallagher explain how a series of sophisticated hacking programs use malware to perform both targeted infiltrations of computers but also broader mass surveillance over entire networks. The Intercept reports:
One implant, codenamed UNITEDRAKE, can be used with a variety of "plug-ins" that enable the agency to gain total control of an infected computer.
An implant plug-in named CAPTIVATEDAUDIENCE, for example, is used to take over a targeted computer's microphone and record conversations taking place near the device. Another, GUMFISH, can covertly take over a computer's webcam and snap photographs. FOGGYBOTTOM records logs of Internet browsing histories and collects login details and passwords used to access websites and email accounts. GROK is used to log keystrokes. And SALVAGERABBIT exfiltrates data from removable flash drives that connect to an infected computer.
The implants can enable the NSA to circumvent privacy-enhancing encryption tools that are used to browse the Internet anonymously or scramble the contents of emails as they are being sent across networks. That's because the NSA's malware gives the agency unfettered access to a target's computer before the user protects their communications with encryption.
It is unclear how many of the implants are being deployed on an annual basis or which variants of them are currently active in computer systems across the world.
Asked to comment by the journalists, Mikko Hypponen, an expert in malware who serves as chief research officer at the Finnish security firm F-Secure, said the implications of the NSA programs were "disturbing" as these kinds of clandestine manipulations can seriously impact the functioning of the web.
"When they deploy malware on systems," Hypponen explained, "they potentially create new vulnerabilities in these systems, making them more vulnerable for attacks by third parties."
The reporting also explains how the NSA has used what are called "man-in-the-middle" techniques as a way to trick computers into giving access to fake servers designed to look like friendly ones. In one example, under a program codenamed QUANTUMHAND, the NSA used a phony server that looked like it was a Facebook server so it could access users computers. According to the reporting:
When a target attempts to log in to the social media site, the NSA transmits malicious data packets that trick the target's computer into thinking they are being sent from the real Facebook. By concealing its malware within what looks like an ordinary Facebook page, the NSA is able to hack into the targeted computer and covertly siphon out data from its hard drive. A top-secret animation demonstrates the tactic in action.
The documents show that QUANTUMHAND became operational in October 2010, after being successfully tested by the NSA against about a dozen targets.
According to Matt Blaze, a surveillance and cryptography expert at the University of Pennsylvania, it appears that the QUANTUMHAND technique is aimed at targeting specific individuals. But he expresses concerns about how it has been covertly integrated within Internet networks as part of the NSA's automated TURBINE system.
"As soon as you put this capability in the backbone infrastructure, the software and security engineer in me says that's terrifying," Blaze says.
"Forget about how the NSA is intending to use it. How do we know it is working correctly and only targeting who the NSA wants? And even if it does work correctly, which is itself a really dubious assumption, how is it controlled?"
____________________________